The FBI. Cybercrime Division or International Cyber Security Protection Alliance infection is a screenlocker from the Troj/Urausy-Ransomware and Reveton family of ransomware infections. When installed this infection does not allow you to access your computer or your files without a paying a ransom. When infected with this Trojan, you will be shown a ransom screen instead of your Windows desktop when you login to Windows. This ransom screen will state that the FBI has detected that your computer has been downloading or distributing copyrighted content or pornography. This infection will display different lock screens depending on what country your computer is currently located in. It is able to detect your country by using the IP address of your computer. This guide will focus on the USA variant of the FBI Cybercrime Division, but the removal guide can be used for any variant of this ransomware.
FBI Cybercrime Division Ransomware screen shot
For more screen shots of this infection click on the image above.
There are a total of 2 images you can view.
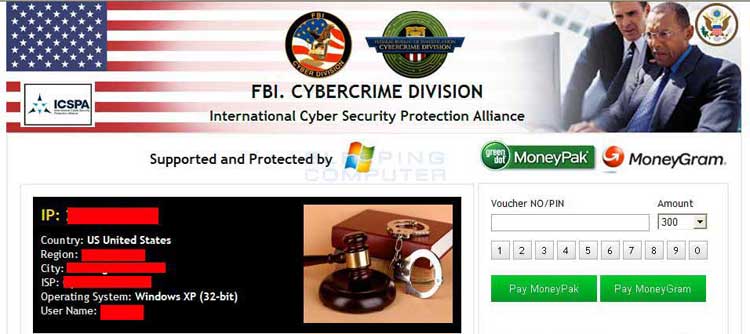
If your computer is connected to the Internet from the United States of America, the screenlocker will state that the FBI Cybercrime Division & International Cyber Security Protection Alliance has locked you out of your computer. This screen continues to state that your computer is breaking copyright laws and possibly distributing pornographic material. It will state that since this is a one-time offense you can pay a fine to gain access to your computer and not face prosecution. It then prompts you to go to a 7-Eleven, Walmart, Rite Aid, Kmart, or CVS and purchase a green dot MoneyPak voucher or a MoneyGram xpress Packet for $300 US dollars. You are then told that you need to input the voucher number into the screenlocker and submit it to gain access to your computer again. Once the malware developers receive the ransom, they will unlock your screen and you will be able to gain access to your desktop again. As it is possible to regain access to your computer without paying the ransom, please do not purchase and send payment and instead follow the instructions below.
The text of the FBI. Cybercrime Division screenlocker pretending to be from the FBI is:
FBI. Cybercrime DivisionInternational Cyber Security Protection Alliance
IP: xxx.xxx.xxxCountry: US United StatesRegion: <Your State>City: <Your City>ISP: <Your ISP>Operating System: <Your Windows Version>: Your Country HereUsername: <Your Login Name>
Attention!Your PC is blocked due to at least one of the reasons specified below.
You have been violation Copyright and Related Rights Law (Video, Music, Software) and illegally using or distributing copyrighted content, thus infringing Article I, Section 2, Clause 8, also known as the Copyright of the Criminal Code of United States of America.Article I, Section 2, Clause 8 of the Criminal Code provides for a fine of 200 to 500 hundred minimal wages or a deprivation of liberty for 2 to 8 years.You have been viewing or distributing prohibited Pornographic content (Child Porn/Zoophilia and etc). Thus violating article 2, Section 1, Clause 2 of the Criminal Code of United States of America. Article 2, Section 1, Clause 2 of the Criminal Code provides for a deprivation of liberty for 4 to 12 years.Illegal access to computer has been initiated from your PC, or you have been...without your knowledge or consent, your PC may be infected by malware, thus you are violating the law of Neglectful Use of Personal Computer. Article 210 of the Criminal Code provides for a fine of up to $100,000 and/or a deprivation of liberty for 4 to 9 years.Pursuant to the amendment to the Criminal Code of United States of America of August 28, 2012, this law infringement (if it is not repeated - first time) may be considered as conditional in case you pay the fine to the State.<Lot's of further pretend legal nonsense followed by>Fines may be paid within 72 hours after the infringement. As soon as 72 hours elapse, the possibility to pay the fine expires, and a criminal case is initiated against you automatically within the next 72 hours!To unblock the computer, you must pay the fine through MoneyPak or MoneyGram xpress Packet of $300.When you pay the fine, your PC will get unlocked in 1 to 72 hours after the money is put into the State's account.Since your PC is unlocked, you will be given 7 days to correct all violations.
Remember that this is a computer infection and your computer has not actually been locked by the FBI or any other government agency. Therefore, ignore this screen and do not pay the ransom. Instead use the free removal guide below to remove the FBI Cybercrime Division ransomware from your computer.
Threat Classification:
Advanced information:
Tools Needed for this fix:
Guide Updates:
03/29/13 - Initial guide creation04/09/13 - Updated to use HitmanPro.Kickstart
- Please print out these instructions as we will need to perform most of these steps on the infected computer. You will also need a USB drive, which will have all of its data erased and will then be formatted. Therefore, only use a USB drive that does not contain any data that you need. This USB drive must also have a size of at least 32 MB.
- As the FBI Cybercrime Division Ransomware infection locks you out of your computer, you will need to create a bootable USB drive that contains the HitmanPro.Kickstart program. We will then boot your computer using this bootable USB drive and use it to clean the infection so that you are able to access Windows normally again.In order to do this please download HitmanPro from the following link and save it to your Windows desktop.When you visit the above page, please download the version that corresponds to the bit-type of the Windows version you will be using to create the Kickstart USB drive.
- Once HitmanPro has been downloaded, please insert the USB key that you would like to erase and use for the installation of HitmanPro.Kickstart.
- Once the USB drive is attached to your computer, double-click on the file named HitmanPro.exe (for 32-bit versions of Windows) orHitmanPro_x64.exe (for 64-bit versions of Windows). When the program starts you will be presented with the start screen as shown below.
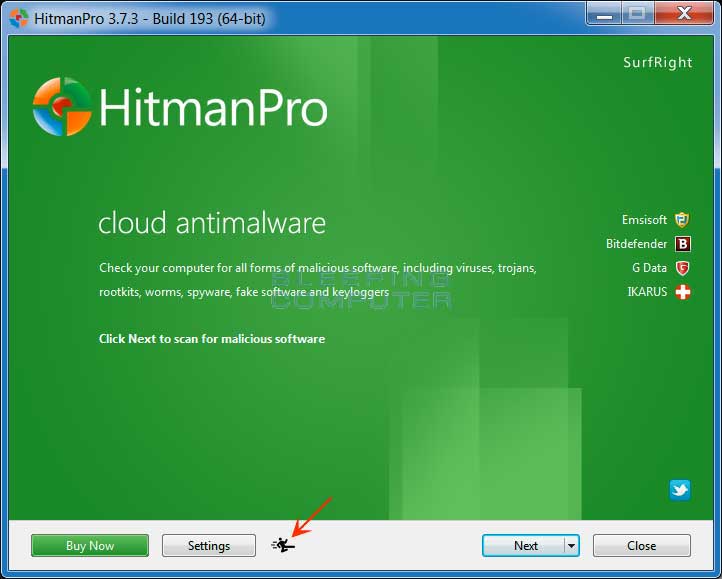 Now click on the little picture of the person performing a kick as indicated by the red arrow above.
Now click on the little picture of the person performing a kick as indicated by the red arrow above. - This will open a screen where you will see some information on how to create the Kickstart USB drive.
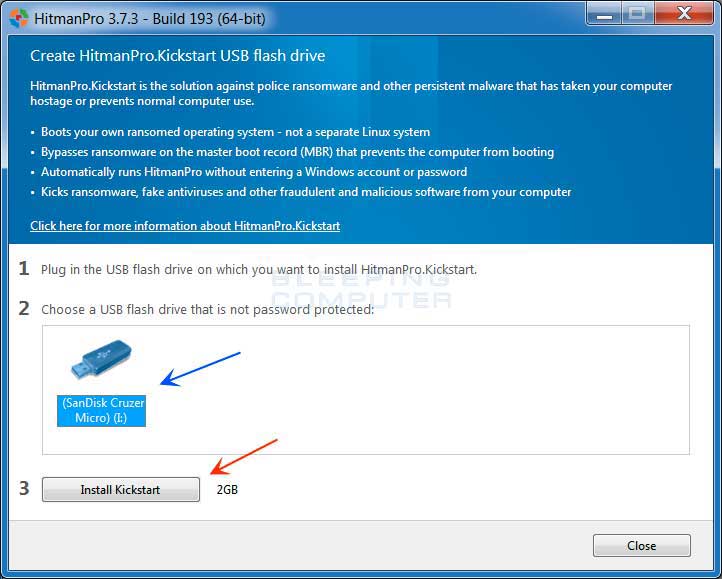 You should also a see a list of all USB drives that are currently attached to your computer as indicated by the blue arrow in the picture above. Select the USB drive that you would like to use and then click on the Install Kickstart button. Please note that this process will erase all of the data on the selected USB drive, so be sure to first backup any data that may be stored on it.
You should also a see a list of all USB drives that are currently attached to your computer as indicated by the blue arrow in the picture above. Select the USB drive that you would like to use and then click on the Install Kickstart button. Please note that this process will erase all of the data on the selected USB drive, so be sure to first backup any data that may be stored on it. - You will now be presented with an alert stating that the USB flash drive will be erased. If you wish to proceed, click on the Yes button. Otherwise, click on the No button to cancel this process. Once you click on the Yes button, the program will begin to download the necessary files and will then install them on the USB Drive. When it has finished you can then click on the Close button to close the HitmanPro program.
- Now remove the Kickstart USB drive and insert it into the infected computer.
- Once it is inserted, turn off the infected computer and then turn it on. As soon as you power it on, look for text on the screen that tells you how to access the boot menu. This text will typically contain a key that they want you to press on your keyboard in order select the device you wish to use to boot your computer. The keys that are commonly associated with enabling the boot menu are F8, F11 or F12. You can see a screen shot of various screens that show you what key to press below.
 Screenshot courtesy of SurfRite.Once you determine the proper key that you need to press to access the Boot Menu, restart your computer again and start immediately tapping that key. Once the boot menu appears, you can select the device you wish to boot your computer from. Please select the USB drive that you have installed HitmanPro.Kickstart on and that is inserted into the infected computer.
Screenshot courtesy of SurfRite.Once you determine the proper key that you need to press to access the Boot Menu, restart your computer again and start immediately tapping that key. Once the boot menu appears, you can select the device you wish to boot your computer from. Please select the USB drive that you have installed HitmanPro.Kickstart on and that is inserted into the infected computer. - Your computer will now boot from the USB drive and automatically load the HitmanPro.Kickstart program. As it loads you will be presented with a screen asking you to select the USB boot options you wish to use.
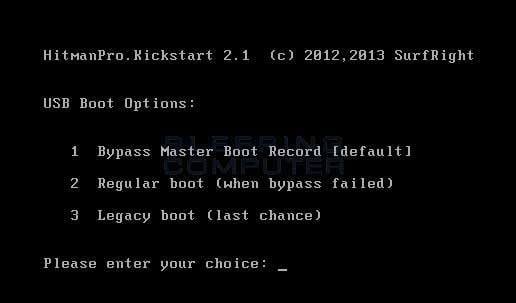 At this screen, please press 1 on your keyboard and you will see that Windows begins to start normally.
At this screen, please press 1 on your keyboard and you will see that Windows begins to start normally. - When Windows starts, you should login as normal and you will once again see the screen locker for the ransomware. After about 15-20 seconds, the HitmanPro window will appear on top of the screen locker as shown in the image below.
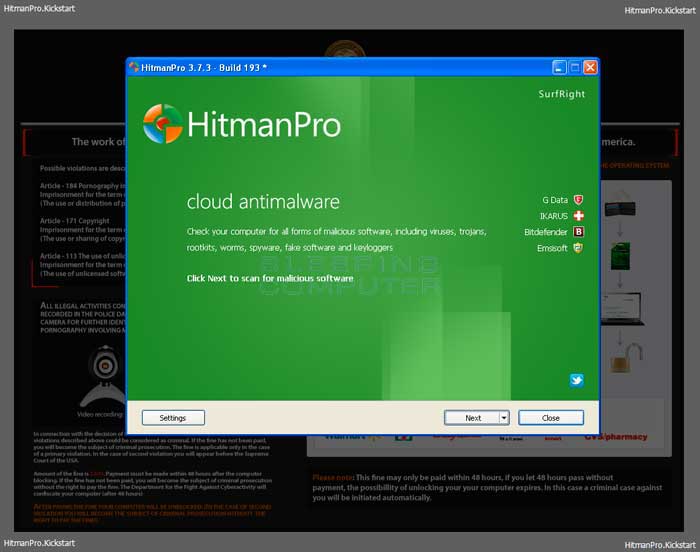 When you see this screen, please click on the Next button to start the cleaning process.
When you see this screen, please click on the Next button to start the cleaning process. - You will now be at the HitmanPro setup screen where you should make sure the option No, I only want to perform a one-time scan to check this computer..
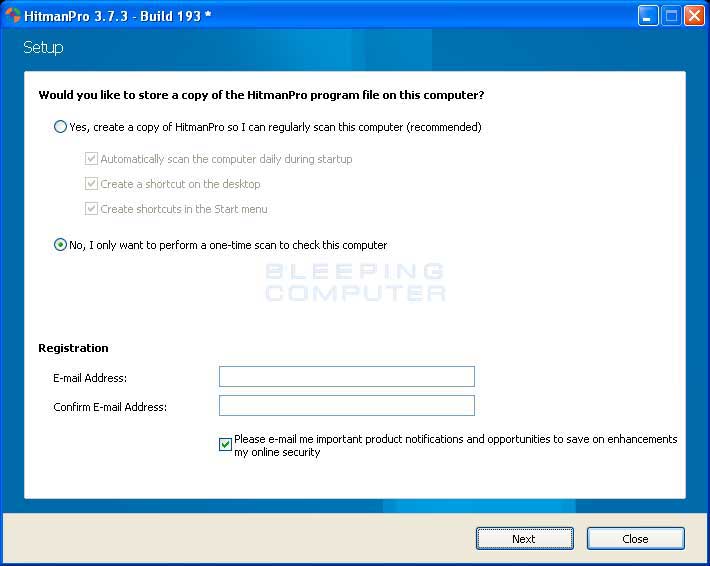 Once it is selected, please click on the Next button.
Once it is selected, please click on the Next button. - HitmanPro will now begin to scan your computer for infections. When it has finished it will display a list of all the malware that the program found as shown in the image below. Please note that the infections found may be different than what is shown in the image.
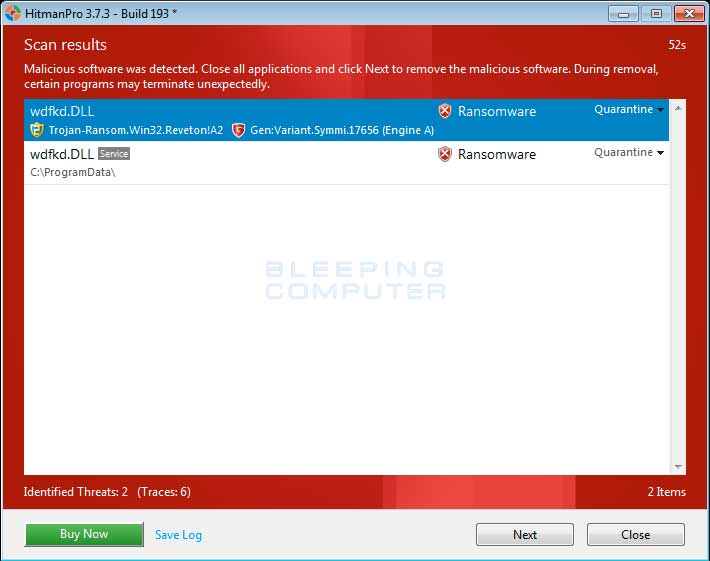 You should now click on the Next button to have HitmanPro remove the detected infections. When it is done you will be shown a Removal Results screen that shows the status of the various infections that were removed. At this screen you should click on the Next button and then on the next screen click on the Reboot button.
You should now click on the Next button to have HitmanPro remove the detected infections. When it is done you will be shown a Removal Results screen that shows the status of the various infections that were removed. At this screen you should click on the Next button and then on the next screen click on the Reboot button. - HitmanPro will now reboot your computer and Windows should start normally. Once it has started, you should login as normal and you will find that the ransomware is no longer active and you can now access your Windows desktop.
- As many malware and unwanted programs are installed through vulnerabilities found in out-dated and insecure programs, it is strongly suggested that you use Secunia PSI to scan for vulnerable programs on your computer. A tutorial on how to use Secunia PSI to scan for vulnerable programs can be found here:
Your computer should now be free of the FBI Cybercrime Division Ransomware infection. If your current anti-virus solution let this infection through, you may want to consider purchasing the licensed version of HitmanPro to protect against these types of threats in the future.
If you are still having problems with your computer after completing these instructions, then please follow the steps outlined in the topic linked below:
Associated FBI Cybercrime Division Ransomware Files:
%AppData%\skype.datFile Location Notes:%AppData% refers to the current users Application Data folder. By default, this is C:\Documents and Settings\<Current User>\Application Data for Windows 2000/XP. For Windows Vista and Windows 7 it is C:\Users\<Current User>\AppData\Roaming.
Associated FBI Cybercrime Division Ransomware Windows Registry Information:
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\shell = "explorer.exe,%AppData%\skype.dat"
This is a self-help guide. Use at your own risk.
BleepingComputer.com can not be held responsible for problems that may occur by using this information. If you would like help with any of these fixes, you can ask for malware removal assistance in our Virus, Trojan, Spyware, and Malware Removal Logs forum.
If you have any questions about this self-help guide then please post those questions in our Am I infected? What do I do? and someone will help you.

No comments:
Post a Comment