The FBI Anti-Piracy Warning MoneyPak Ransomware is a computer infection that locks your screen until you send them a ransom in the form of a GreenDot MoneyPak payment. This lock screen, which is displayed below, will be shown when you login to Windows and will not allow access to the Windows desktop, your files, or your applications. To remove this lock screen you are required to pay a ransom of $400 in the form of a MoneyPak voucher code. Once you submit the code and its verified, your screen will be unlocked and the infection will be removed. As it is possible to remove this infection without paying the ransom, please do not go out and purchase the requested MoneyPak.
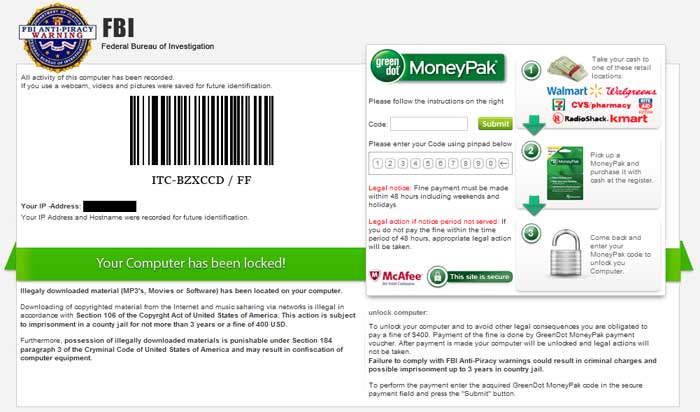
FBI Anti-Piracy MoneyPak Ransomware screen shot
For more screen shots of this infection click on the image above.
There are a total of 1 images you can view.
The lock screen from this infection pretends to be an alert from the Federal Bureau of Investigations (FBI) who has detected that your computer contains illegal and copyrighted software. It then states that due to this illegal content your computer has been locked until you pay a fine of $400 in the form of a MoneyPak voucher payment. They also state that if you do not pay the payment in 48 hours, you will face legal action from FBI. Once you send them the MoneyPak voucher code your computer would then be unlocked and the infection deleted. Last, but not lease, this infection will continuously play a fake recording from the FBI. The reality is that this is a computer infection and has nothing to do with the FBI or any other legal authority. Therefore, please ignore anything the lock screen says.
The text of this lock screen is:
FBI Anti-Piracy Warning
All activity of this computer has been recorded.
If you use a webcam, videos and pictures were saved for future identifications.
Your Computer has been locked!
Illegal downloaded material (MP3's, Movies or Software) has been located on your computer.
Unlock your computer:
To unlock your computer and yo avoid other legal consequences you are obligated to pay a fine of $400. Payment of the fine is done by GreenDot MoneyPak payment voucher. After payment is made your computer will be unlocked and legal actions will not be taken.
Failure to comply with FBI Anti-Piracy warnings could result in criminal charges and possible imprisonment up to 3 years in country jail.
The text of the recorded audio alert is:
FBI Warning. Your computer is blocked for violation of federeal law.
As you can see this is a computer infection and not an actual alert from the FBI. Therefore, please do not purchase a MoneyPak and send the ransom payment. Instead you should use the removal guide below to remove this infection and other malware from your computer for free.
Threat Classification:
Advanced information:
View FBI Anti-Piracy Warning MoneyPak Ransomware files.
View FBI Anti-Piracy Warning MoneyPak Ransomware Registry Information.
Tools Needed for this fix:
Symptoms that may be in a HijackThis Log:
O4 - HKCU\..\Run: [<random>] C:\WINDOWS\<random>.exe
Guide Updates:
12/22/12 - Initial guide creation
Automated Removal Instructions for FBI Anti-Piracy Warning MoneyPak Ransomware using Emsisoft Anti-Malware:
- Print out these instructions as we will need to reboot your computer into Safe mode with Networking and you may not have access to your web browser for part of this process.
- This infection makes it difficult to access your documents and programs because it locks the screen. In order to bypass this locker, we need to reboot into Safe Mode with Networking. To do this, perform the following steps for your version of Windows:
Windows 8: Please follow the steps in this guide to restart your computer in Windows 8 Safe Mode.
Windows XP, Vista, and 7: Turn your computer off and then back on and when you see anything on the screen, immediately start tapping the F8key on your keyboard. Eventually you will be brought to a menu similar to the one below: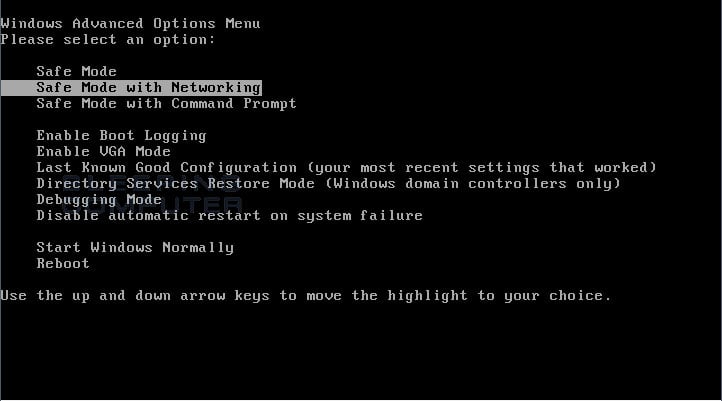
Using the arrow keys on your keyboard, select Safe Mode with Networking and press Enter on your keyboard. If you are having trouble entering safe mode, then please use the following tutorial:
How to start Windows in Safe Mode
Windows will now boot into safe mode with networking and prompt you to login as a user. - When you are prompted to login, please login as the user that is infected with FBI Anti-Piracy Warning MoneyPak Ransomware.
- Before we can do anything we must first end the processes that belong to FBI Anti-Piracy Warning MoneyPak Ransomware and other infections so that they does not interfere with the cleaning procedure. To do this please download RKill to your desktop from the following link.
RKill Download Link - (Download page will open in a new tab or browser window.)
When at the download page, click on the Download Now button labeled iExplore.exe download link. When you are prompted where to save it, please save it on your desktop. - Once it is downloaded, double-click on the iExplore.exe icon in order to automatically attempt to stop any processes associated with FBI Anti-Piracy Warning MoneyPak Ransomware and other Rogue programs. Please be patient while the program looks for various malware programs and ends them. When it has finished, the black window will automatically close and you can continue with the next step. If you get a message that RKill is an infection, do not be concerned. This message is just a fake warning given by FBI Anti-Piracy Warning MoneyPak Ransomware when it terminates programs that may potentially remove it. If you run into these infections warnings that close RKill, a trick is to leave the warning on the screen and then run RKill again. By not closing the warning, this typically will allow you to bypass the malware trying to protect itself so that RKill can terminate FBI Anti-Piracy Warning MoneyPak Ransomware . So, please try running RKill until the malware is no longer running. You will then be able to proceed with the rest of the guide. Do not reboot your computer after running RKill as the malware programs will start again.
If you continue having problems running RKill, you can download the other renamed versions of RKill from the RKill download page. Both of these files are renamed copies of RKill, which you can try instead. Please note that the download page will open in a new browser window or tab. - Now download and save the Emsisoft Anti-Malware setup program to your desktop from the link below:
http://www.emsisoft.com/en/software/antimalware/download/
The download is fairly large, so please be patient while it downloads. - Once the file has been downloaded, double-click on the EmsisoftAntiMalwareSetup.exe icon to start the program. If Windows Smart Screen issues an alert, please allow it to run anyway.
If the setup program displays an alert about safe mode, please click on the Yes button to continue. You should now see a dialog asking what language you would like to use. Please select the language you wish to use and press the OK button. - You will eventually get to a screen asking the mode that you wish to use Emsisoft Anti-Malware.
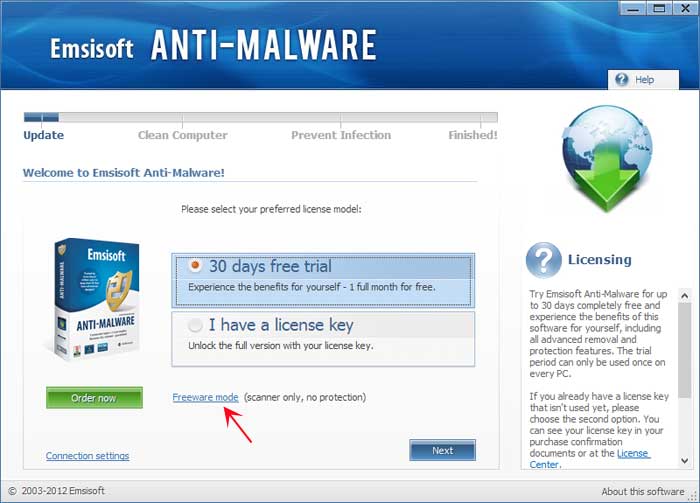
If you wish to try the 30 days free trial, then select that option and press the Next button. If you wish to use the free version, which can scan and delete but not provide real-time protection, click on the Freeware mode link as shown by the red arrow in the image above. - You will now be at a screen asking if you wish to join Emsisoft's Anti-Malware network. Read the descriptions and uncheck the options that you wish to use. When you are ready click on the Next button.
- Emsisoft Anti-Malware will now begin to update it's virus detections.
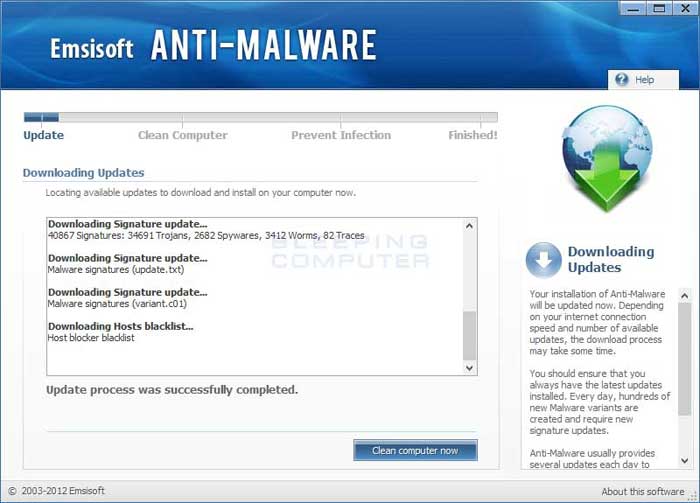
Please be patient as it may take a few minutes for the updates to finish downloading. - When the updates are completed, click on the Clean computer now button. Emsisoft Anti-Malware will start to load its scanning engine and then display a screen asking what type of scan you would like to perform.
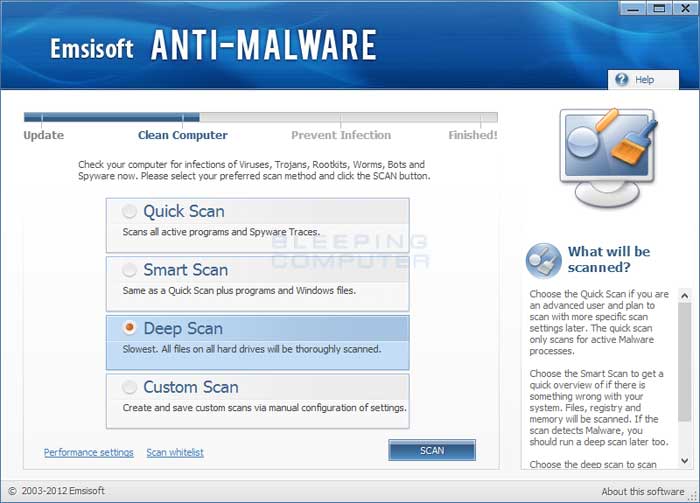
Please select the Deep Scan option and then click on the Scan button. The Deep Scan option will take the longest time to scan your computer, but will also be the most thorough. As you are here to clean infections, it is worth the wait to make sure your computer is properly scanned. - Emsisoft Anti-Malware will now start to scan your computer for rootkits and malware.
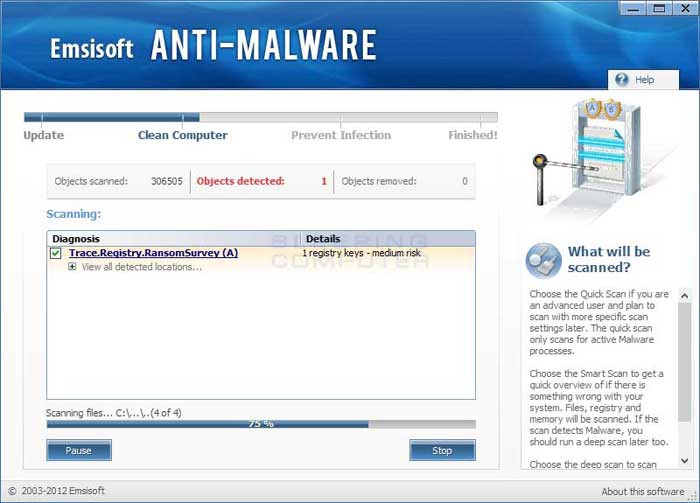
Please be patient while Emsisoft Anti-Malware scans your computer. - When the scan has finished, the program will display the scan results that shows what infections where found.
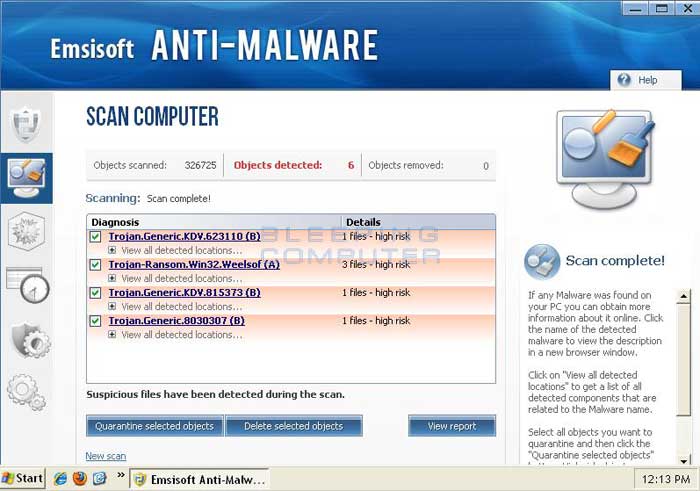
Now click on the Quarantine Selected Objects button, which will remove the infections and place them in the program's quarantine. You will now be at the last screen of the Emsisoft Anti-Malware setup program, which you can close. If Emsisoft prompts you to reboot your computer to finish the clean up process, please allow it to do so. - Please reboot your computer into the normal Windows mode and when you are back at your normal Windows desktop or Windows Start Screen please continue with the next step.
- As this infection is known to be installed by vulnerabilities in out-dated and insecure programs, it is strongly suggested that you use Secunia PSI to scan for vulnerable programs on your computer. A tutorial on how to use Secunia PSI to scan for vulnerable programs can be found here:
How to detect vulnerable and out-dated programs using Secunia Personal Software Inspector
Your computer should now be free of the FBI Anti-Piracy Warning Ransomware infection. If your current anti-virus solution let this infection through, you may want to consider purchasing the full version of Emsisoft Anti-malware to protect your computer against these types of threats in the future.
If you are still having problems with your computer after completing these instructions, then please follow the steps outlined in the topic linked below:
Associated FBI Anti-Piracy Warning MoneyPak Ransomware Files:
%CommonAppData%\<random>
%CommonAppData%\<random>.exe
%CommonAppData%\<random>\
%CommonAppData%\<random>\arr-next.gif
%CommonAppData%\<random>\bg.wav
%CommonAppData%\<random>\b-sep.gif
%CommonAppData%\<random>\btn.png
%CommonAppData%\<random>\btn-sq.gif
%CommonAppData%\<random>\cam-place.bmp
%CommonAppData%\<random>\card.jpg
%CommonAppData%\<random>\green-l.png
%CommonAppData%\<random>\green-r.png
%CommonAppData%\<random>\ie7.css
%CommonAppData%\<random>\larr.gif
%CommonAppData%\<random>\lock.png
%CommonAppData%\<random>\locked-text-en.png
%CommonAppData%\<random>\logo-img.png
%CommonAppData%\<random>\logo-text.gif
%CommonAppData%\<random>\main.html
%CommonAppData%\<random>\mainbg.gif
%CommonAppData%\<random>\mcafee-lock.png
%CommonAppData%\<random>\money.gif
%CommonAppData%\<random>\moneypak.png
%CommonAppData%\<random>\payments-en.png
%CommonAppData%\<random>\side-block.png
%CommonAppData%\<random>\step.gif
%CommonAppData%\<random>\step.png
%CommonAppData%\<random>\style.css
%CommonAppData%\<random>\wait.html
%WinDir%\<random>.exeFile Location Notes:
%Windir% refers to the Windows installation folder. By default, this is C:\Windows for Windows 95/98/ME/XP/Vista/7/8 or C:\Winnt for Windows NT/2000.
%CommonAppData% refers to the Application Data folder for the All Users Profile. By default, this is C:\Documents and Settings\All Users\Application Data for Windows 2000/XP and C:\ProgramData\ in Windows Vista, Windows 7, and Windows 8.
%CommonAppData% refers to the Application Data folder in the All Users profile. For Windows XP, Vista, NT, 2000 and 2003 it refers to C:\Documents and Settings\All Users\Application Data\, and for Windows Vista, Windows 7, and Windows 8 it is C:\ProgramData.
Associated FBI Anti-Piracy Warning MoneyPak Ransomware Windows Registry Information:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "<random>" = "C:\WINDOWS\<random>.exe;"
This is a self-help guide. Use at your own risk.
BleepingComputer.com can not be held responsible for problems that may occur by using this information. If you would like help with any of these fixes, you can ask for malware removal assistance in our Virus, Trojan, Spyware, and Malware Removal Logs forum.
If you have any questions about this self-help guide then please post those questions in our Am I infected? What do I do? and someone will help you.

No comments:
Post a Comment